12+ Isms Agreement
And would it lead to reconciliation or would the inevitable inequities produce all the more resentment. What is the objective of Annex A152 of ISO 270012013.
Iso 27001 Annex A 15 Supplier Relationships
Secret authentication information is a gateway to access valuable assets.

. Agreement of Corporation signed between CEPE Kathmandu University Nepal and LAPLACE Université Toulouse III - Paul Sabatier. SF 9424-EFT PDF Nonemployee Expense Voucher. Tape Data Recovery Retrives data from all types and capacities of tape drives including LTO 1 LTO 2 LTO 3.
How to track emails in Exchange Server via Message-ID. There is partisan agreement on Prop 26. Cyber Defense SOAR STORM.
Who would represent each group and how would such an agreement be enforced. SF 6432-H PDF Performance Bond. 12 December 2019.
A924 Management of Secret Authentication Information of Users. SF 6432-I PDF Quotation Bond. David Alan Mamet ˈ m æ m ɪ t.
Yuan Shikai crackdown the Chinese National Assembly. So needs to be controlled through a formal management process and needs to be kept confidential to the user. File Erasure Permanently wipe files and folders and.
May 21 2012 By John Frame. ISO 270022013 iswas a code of practice for an information security management system ISMS and delves into a much higher level of detail than the Annex A Controls of ISO 27001 containing security techniques control objectives security requirements access control information security risk treatment controls personal and proprietary. Racisms Sexisms and Other Isms.
OTRS is a highly customizable Software Solution for Customer Service Management ITSM ISMS SOAR Cyberdefense and more. ISOIEC 27002 is an information security standard published by the International Organization for Standardization ISO and by the International Electrotechnical Commission IEC titled Information security cybersecurity and privacy protection Information security controls. Late 1913 January 1914.
The European Union EU is an economic and political union of 27 countriesIt operates an internal or single market which allows free movement of goods capital services and people between. 02-2100-3043 월금 9001800 공휴일 제외. Fewer than four in ten Democrats Republicans and independents would vote yes Moreover less than a majority across all regions and demographic groupswith the.
Electronic Funds Transfer Agreement. Get breaking MLB Baseball News our in-depth expert analysis latest rumors and follow your favorite sports leagues and teams with our live updates. I the one-year prohibition on seeking or accepting employment or any form of compensation or financial benefit from any contractor or vendor with whom a former staff member has had personal.
Virtual Machine Recovery Recover documents multimedia files and database files from any virtual machine. The terms and conditions set forth in the EBSCO License Agreement are made part of this purchase order and are in lieu of all terms and. 10-Nov-2022 Shahjalal Islami Bank donates 75000 seventy-five thousand pcs.
Annex A152 is about supplier service development management. Paper on Engineering Education at KU received an international award 5 December 2019. The objective in this Annex A control is to ensure that an agreed level of information security and service delivery is maintained in line with supplier agreements.
SF 6432-K PDF SandiaNTESS Retiree. The organisation must supervise and monitor the activity of outsourced system development. The described solution requires Microsoft Exchange Server 2007 or newer.
It is an interdisciplinary field that draws inspiration from various disciplines both within and outside. Qing general Yuan Shikai by agreement with Sun Yat-sen and his Provisional Government Emperor Puyi to abdicate and established the Beiyang government ending the Qing Dynasty. Colonialism is a practice or policy of control by one people or power over other people or areas often by establishing colonies and generally with the aim of economic dominance.
It includes the examination of educational theories the presuppositions present in them and the arguments for and against them. Californias Water Balancing Act November 18. December 1 2022 1200 pm - 100 pm View All.
The philosophy of education is the branch of applied philosophy that investigates the nature of education as well as its aims and problems. If the Licensee andor Sites use purchase orders in conjunction with this Agreement then the Licensee andor Sites agree that the following statement is hereby automatically made part of such purchase orders. Of Blankets to Honble Prime Ministers Relief Fund.
The Duck Variations Sexual Perversity in Chicago and. 우03171 서울특별시 종로구 세종대로 209 정부서울청사 개인정보보호위원회. Soviet Union in full Union of Soviet Socialist Republics USSR Russian Soyuz Sovetskikh Sotsialisticheskikh Respublik or Sovetsky Soyuz former northern Eurasian empire 1917221991 stretching from the Baltic and Black seas to the Pacific Ocean and in its final years consisting of 15 Soviet Socialist Republics SSRs.
SF 4601-C MS Excel Payment Bond. When you know a Message-ID you can track all emails with that particular Message-ID and get various information on the flow of these emails eg. This is where Annex A 151 is important to have correct as well as.
A1521 Monitoring Review of Supplier Services. 12-Nov-2022 Shahjalal Islami Bank organized School Banking Conference-2022 at Kalapara in Patuakhali district as lead Bank. Individual lesson - 15 euros 1 lesson 60 minutes ZOOM Minigroup 2 people 10 lessons - 90 euros for 1 student ZOOM Classes for children.
The perfect SOAR solution for fast Security Orchestration Automation and Incident Response. Data Recovery Recover lost or deleted data from HDD SSD external USB drive RAID. In the process of colonisation colonisers may impose their religion language economics and other cultural practicesThe foreign administrators rule the territory in pursuit of their interests seeking to.
Annex A12 Operations Security Annex A122 Protection from Malware Annex A123 Backup Annex A124 Logging and Monitoring Annex A125 Control of Operational Software Annex A126 Technical Vulnerability Management Annex A127 Information Systems Audit Considerations Annex A13 Communications Security Annex A132 Information Transfer. Hello everyone My name is Olga I am a native speaker a certified teacher of Russian as a foreign language. Where system and software development is outsourced either wholly or partly to external parties the security requirements must be specified in a contract or attached agreement.
The ISOIEC 27000-series standards are descended from a corporate security standard donated by. 12 suggests a similar way of looking at the natural gifts in the human race. A service level agreement SLA is a general agreement between a customer and a service.
Born November 30 1947 is an American playwright filmmaker and authorHe won a Pulitzer Prize and received Tony nominations for his plays Glengarry Glen Ross 1984 and Speed-the-Plow 1988. He first gained critical acclaim for a trio of off-Broadway 1970s plays. It typically includes passwords encryption keys etc.

Isms Doc A15 1 Information Security Policy For Supplier Relationships By Certikit Limited Issuu

Iso 27001 2013 Isms

What Is An Information Security Management System Isms Centraleyes

Isms Connect

Iso 27001 Annex A 15 Supplier Relationships

Pdf Comparison Of It Security Standards Nikolay Nikolaev Academia Edu
Iso 27001 Annex A 15 Supplier Relationships
Iso 27001 Annex A 15 Supplier Relationships

Annex A 12 Operations Security Dataguard
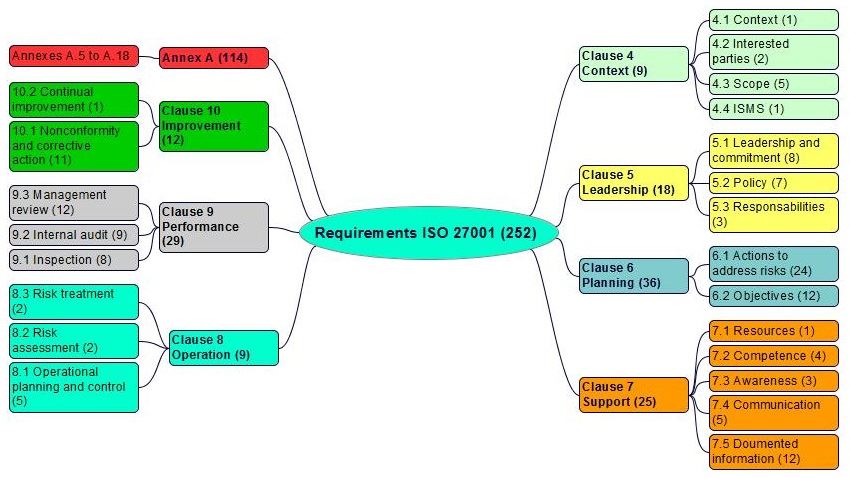
Iso 27001 Requirements Version 2013

Isms Information Security Management System Isms Manual

Isms Connect
Iso 27001 Annex A 15 Supplier Relationships

What Is An Information Security Management System Isms Myra
Iso 27001 Annex A 15 Supplier Relationships

Isms Connect
Interested Parties Management Isms Online